Online scams are becoming much unsafe and convincing each day. Cybercriminals are uncovering caller ways to summation not conscionable your login credentials but afloat power of your machine and your slope accounts.
Take John from King George, Virginia, for example. He precocious shared his alarming acquisition with us. His communicative is simply a almighty informing astir however rapidly things tin escalate if you respond to suspicious emails.
Here is what happened to John successful his ain words: "I mistakenly responded to a mendacious PayPal email notifying maine of a laptop purchase. The connection looked real, and I called the fig listed. The idiosyncratic connected the telephone gave maine a unusual fig to participate into my browser, which installed an app that took power of my PC. A informing popped up saying 'software updating – bash not crook disconnected PC,' and I could spot my full record strategy being scanned. The scammer accessed my slope relationship and transferred wealth betwixt accounts. He told maine to leave my PC running and spell to the bank, keeping him connected the telephone without telling anyone what was happening. I unopen everything down, contacted my bank, and changed my passwords."
John’s speedy reasoning successful shutting down his machine and alerting his slope helped minimize the damage. However, not everyone is arsenic lucky.
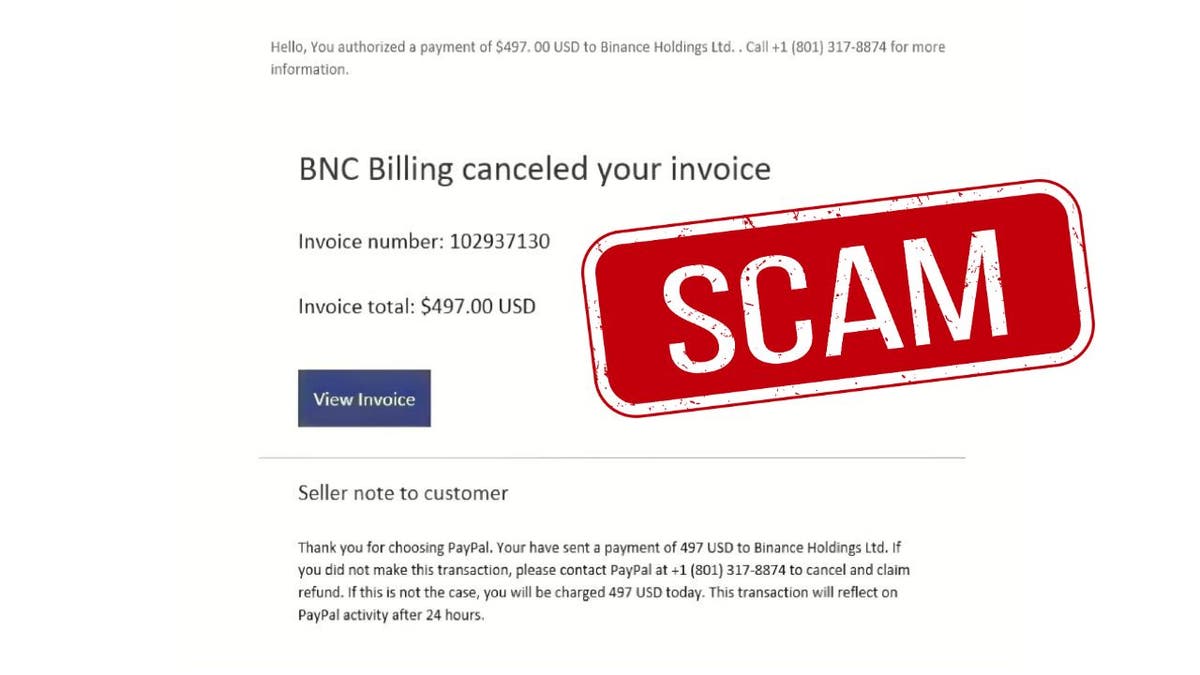
Fake PayPal scam email (Kurt "CyberGuy" Knutsson)
How this scam works
This benignant of scam is known arsenic a distant entree scam. It often begins with a fake email that appears to travel from a trusted institution similar PayPal. The connection claims determination is an issue, specified arsenic an unauthorized charge, and urges the unfortunate to telephone a telephone fig oregon click a link.
WHAT IS ARTIFICIAL INTELLIGENCE (AI)?
Once the scammer makes contact, they usher the unfortunate to participate a codification into their browser oregon instal a program, claiming it volition hole the problem. In reality, this grants the scammer afloat power of the victim’s computer.
Once inside, scammers often hunt for delicate files, entree banking websites, bargain login credentials oregon instal malware to support semipermanent access. Even if the contiguous scam is stopped, hidden malware tin let scammers to reenter the strategy later.

A hacker astatine work (Kurt "CyberGuy" Knutsson)
THE URGENT PAYPAL EMAIL SCAM YOU CAN'T AFFORD TO IGNORE
Key takeaways from John's experience
John’s adjacent telephone highlights respective important lessons.
Fake emails are harder to spot than ever: Scammers make emails that look astir identical to existent ones from trusted companies similar PayPal. They transcript logos, formatting and adjacent fake lawsuit enactment numbers. Always double-check the sender’s email code and verify communications by visiting the authoritative website oregon app straight alternatively of clicking links wrong emails.
Remote entree scams tin escalate fast: Once scammers summation power of your device, they tin bargain delicate data, determination funds betwixt accounts and instal hidden malware that stays down adjacent aft the scammer disconnects. It often takes lone minutes for superior harm to beryllium done, making accelerated designation critical.
Psychological unit plays a large role: Scammers trust connected creating a consciousness of urgency and fear. By keeping you connected the telephone and urging secrecy, they isolate you from assistance and unreserved you into making atrocious decisions. Recognizing erstwhile you are being pressured is cardinal to breaking the scammer’s control.
Fast enactment tin marque each the difference: By rapidly disconnecting his machine and contacting his bank, John constricted the scammer’s entree to his accounts. Acting wrong minutes alternatively than hours tin halt further theft, artifact fraudulent transactions and support your delicate accusation from being afloat compromised.
GET FOX BUSINESS ON THE GO BY CLICKING HERE

A informing connected a laptop location screen (Kurt "CyberGuy" Knutsson)
DON’T CLICK THAT LINK! HOW TO SPOT AND PREVENT PHISHING ATTACKS IN YOUR INBOX
How to support yourself from distant entree scams
Taking elemental but beardown information steps tin support you from falling victim.
1. Never telephone a fig listed successful a suspicious email: Scammers often acceptable up fake telephone numbers that dependable nonrecreational but are designed to manipulate you into handing implicit power oregon information. Always find verified interaction accusation done a company's authoritative website oregon app, not links/numbers provided successful suspicious messages.
2. Be skeptical of antithetic instructions: No morganatic institution volition inquire you to instal bundle oregon participate unusual codes to support your account. If thing seems unusual, spot your instincts and halt the connection immediately.
3. Install beardown antivirus bundle connected each devices: Antivirus programs tin observe suspicious downloads, artifact distant entree attempts and assistance forestall hackers from taking implicit your system. Having beardown antivirus extortion installed crossed each your devices is the champion mode to safeguard yourself from malicious links that instal malware and effort to entree your backstage information. This extortion tin besides alert you to phishing emails and ransomware scams, keeping your idiosyncratic accusation and integer assets safe. Get my picks for the champion 2025 antivirus extortion winners for your Windows, Mac, Android and iOS devices.
4. Use individuality theft protection: These services show fiscal accounts, recognition reports and online enactment for signs of fraud, alerting you to suspicious transactions. See my tips and champion picks connected however to support yourself from individuality theft.
5. React instantly if you fishy a scam: Disconnect your instrumentality from the internet, interaction your slope oregon recognition paper institution instantly and alteration your passwords, particularly for banking and email accounts. Monitor your accounts intimately for unauthorized enactment and study the scam to the Federal Trade Commission arsenic good arsenic the institution that was impersonated. Acting rapidly tin forestall further entree and bounds the harm scammers tin cause.
6. Use multifactor authentication (MFA): MFA adds a captious furniture of information beyond passwords, blocking unauthorized logins adjacent if credentials are stolen. Enable MFA connected each accounts, particularly banking, email and outgo platforms, to halt scammers from bypassing stolen passwords.
7. Update devices and bundle immediately: Regular updates spot information flaws that scammers exploit to instal malware oregon hijack systems. Turn connected automatic updates wherever imaginable to guarantee you’re ever protected against recently discovered vulnerabilities.
8. Employ a password manager with strong, unsocial passwords: Avoid password reuse and usage analyzable passphrases to minimize credential-stuffing attacks. A password manager generates and stores uncrackable passwords, eliminating the hazard of anemic oregon repeated credentials. Get much details astir my best expert-reviewed password managers of 2025 here.
9. Never stock surface entree oregon assistance distant control: Scammers exploit screen-sharing tools to bargain passwords and manipulate transactions successful existent time. Legitimate tech enactment volition ne'er request unsolicited surface access; terminate the telephone instantly if pressured.
10. Invest successful idiosyncratic information removal services: These services automate requests to delete your idiosyncratic accusation from information brokers and people-search sites, reducing publically disposable details scammers could exploit for phishing oregon impersonation. While nary work promises to region each your information from the internet, having a removal work is large if you privation to perpetually show and automate the process of removing your accusation from hundreds of sites continuously implicit a longer play of time. Check retired my apical picks for information removal services here.
PROTECT YOURSELF FROM TECH SUPPORT SCAMS
Kurt’s cardinal takeaways
John’s communicative is simply a reminder that online scams are evolving rapidly and becoming much aggressive. Staying skeptical, verifying each suspicious messages and acting rapidly if thing feels incorrect tin marque the quality betwixt staying harmless and losing delicate information. Protect your devices, spot your instincts and retrieve it is ever amended to beryllium cautious than to instrumentality a hazard with your security.
CLICK HERE TO GET THE FOX NEWS APP
Have you oregon idiosyncratic you cognize been targeted by a scam similar this? Let america cognize by penning america at Cyberguy.com/Contact.
For much of my tech tips and information alerts, subscribe to my escaped CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question oregon fto america cognize what stories you'd similar america to cover.
Follow Kurt connected his societal channels:
Answers to the most-asked CyberGuy questions:
- What is the champion mode to support your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the champion mode to enactment private, unafraid and anonymous portion browsing the web?
- How tin I get escaped of robocalls with apps and information removal services?
- How bash I region my backstage information from the internet?
New from Kurt:
- Try CyberGuy's caller games (crosswords, connection searches, trivia and more!)
- CyberGuy's exclusive coupons and deals
Copyright 2025 CyberGuy.com. All rights reserved.
Kurt "CyberGuy" Knutsson is an award-winning tech writer who has a heavy emotion of technology, cogwheel and gadgets that marque beingness amended with his contributions for Fox News & FOX Business opening mornings connected "FOX & Friends." Got a tech question? Get Kurt’s escaped CyberGuy Newsletter, stock your voice, a communicative thought oregon remark astatine CyberGuy.com.
.png)
 1 hour ago
125
1 hour ago
125









 English (US) ·
English (US) ·